
Challenges of securing information.
For the IT security professional it is a 24-7 job fighting cyber criminals that want to inflict pain on computers, networks and their users. It is a job that requires constant vigilance and many security firms run network monitoring centers to keep an eye on their customers' networks and the shifting tide of computer vandalism and crime. It is like trench warfare. To open this topic, click on the image to the left.
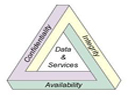
What is information security?
In a nutshell, security is to protect oneself from harm. Information security is also to protect oneself from harm, the only differences is the harm that we are trying to prevent comes in a digital format vs. a physical or verbal format. To open this topic, click on the image to the left.

Who are the attackers?
Computer attackers can be divided into several categories. This discussion will identify these categories. To open this topic, click on the image to the left.

Attacks
There are 5 basic steps that most attackers take to penetrate a computer. This discussion will explore these steps. To open this topic, click on the image to the left.
 Assess the meaning and relevancy of security
Assess the meaning and relevancy of security