What is Information security?
Before we continue on our security mission, you must know what information security is. You must know the terminology and you must know why it is critically important today.
In a nutshell, security is to protect oneself from harm. Information security is also to protect oneself from harm, the only differences is the harm that we are trying to prevent comes in a digital format vs. a physical or verbal format. It is the digital format that computers and networks speak. This is called data and is what we must protect, hence the term Information Security.
The CIA Triangle
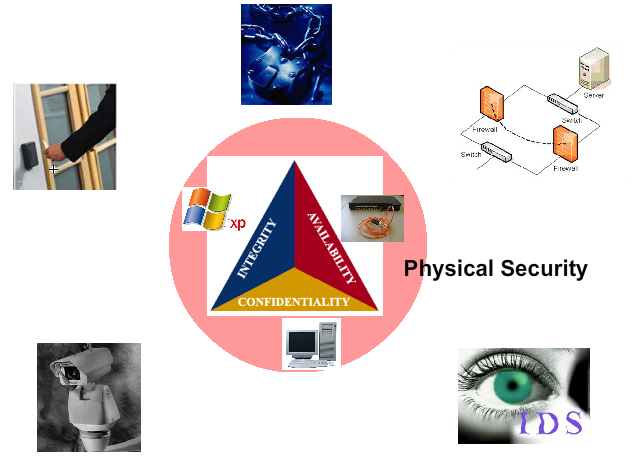
In a more granular sense, Information Security has three unique characteristics that have to be protected and will be the focus of this course, they include: Confidentiality, Integrity and Availability (CIA). Review the definitions of these three characteristics.
Availability: Information certainly has to be secure, but it also has to be immediately available to you when you need it, if you have authorization to use it.
Integrity: When digital information is allowed to be kept intact and not disturbed by aunauthorized people or malicious software then the integrity of the information has been protected.
Confidentiality: When a select group of people, which could be just you, are the only ones given authorization to view information, then the confidentiality of the information must be protected.

Support Systems
With the protection of information, the protection of support systems must also be included. These include the following major support system components:

Communication Systems

Operating Systems

Computer Systems
Layered Protection
Physical Security
Information and the hardware and software that support it are what is protected. The protection comes in multiple layers. The inner most layer is physical security. This includes door locks, surveillance cameras, intrusion detection systems, firewalls, and such.
See image below.
Personnel Security
The next layer is personnel security – this of course deals with people. People must use the proper tools and techniques and follow corporate guidelines regarding security; otherwise absolutely NOTHING can be kept secure. It is said time and time again that this layer is the weakest of all the protection layers. See image below.

Organizational Layer
The last layer is the organizational layer – this is the layer where the policies and procedures are located. This is the layer that essentially guides the personnel security layer, and it is the personnel layer that implements the physical layer. You can see that these are all connected and interact. Securing the center requires that all three layers are implemented consistently and correctly.
See image below.

Information Security Terminology
This tutorial has already given you some terms that are likely new to you. There are terms, however, that are very commonly referred to when discussing information security. These are defined in user-friendly terms below.
Asset and Risk
Let’s assume that one day I park my car in the parking lot. I purposely leave my laptop in the car and lock the car; however, I forget to close my window before I walk off to my office. In this scenario I just defined both an asset and a risk. See the images below.

Threat Agent
That day a man dressed like a thief (maybe that’s because he was one) approached my car. This man is a threat agent. He has the power and potential to steal my assets from me if he so chooses. See image below.

Vulnerability
Normally, the parking lot is very secure, however, that day the parking lot security man was sleeping. This sleeping man created a vulnerability or weakness in the security of the parking lot that will allow the threat agent (the man looking like a thief) to bypass security and rip me off. See image below.

Exploit
Well, the man that looked like a thief actually became one. He chose to steal my laptop by exploiting the security weakness (vulnerability). Fortunately, he did not steal my car. See image below.
 Exploit
Exploit
Importance of Information Security
 Topic 1-2: Discuss the importance of information security in our modern world - student led discussion. Click on the image to the left to review the instructions.
Topic 1-2: Discuss the importance of information security in our modern world - student led discussion. Click on the image to the left to review the instructions.
 Assess the meaning and relevancy of security
Assess the meaning and relevancy of security