Challenges of Securing Information
Today’s Security Attacks
For the IT security professional it is a 24-7 job fighting cyber criminals that want to inflict pain on computers, networks and their users. It is a job that requires constant vigilance and many security firms run network monitoring centers to keep an eye on their customers' networks and the shifting tide of computer vandalism and crime.
 Topic 1-1: Today's Attacks - student led discussion. Click on the image to the left to review the instructions.
Topic 1-1: Today's Attacks - student led discussion. Click on the image to the left to review the instructions.
Difficulties in Defending Against Attacks
It is a challenge to everyone that works (or plays) on computers, to not have a worry about security. Of course you can almost reach 100% security if you never connect your computer to a network (wired or wireless) and never attach a removable device to that computer.
Because of the number of potential security attacks and the speed by which they happen, it is very difficult to manage security.
Speed
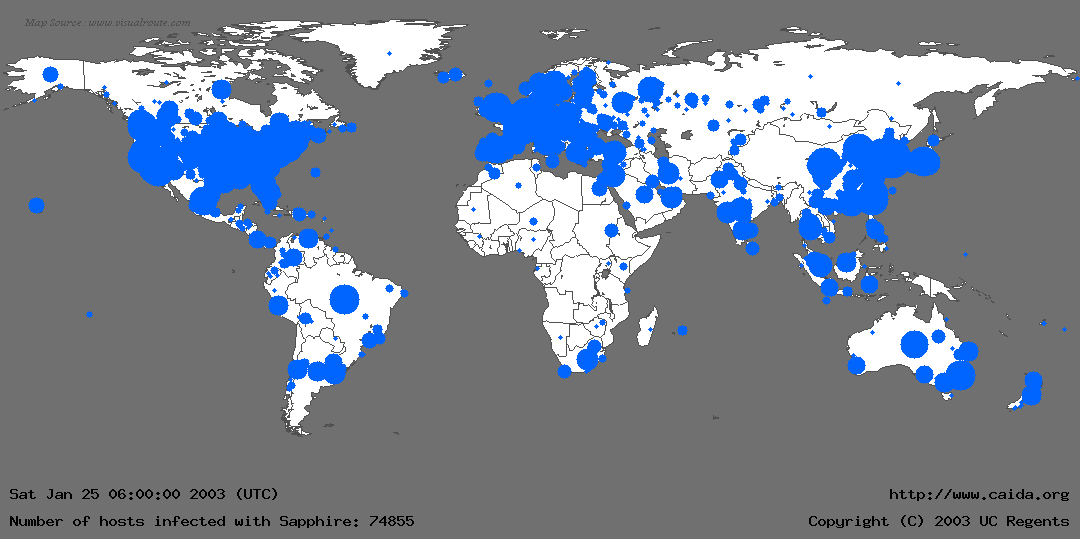
We are a global economy. Attacks can rapidly spread to thousands of victims in just minutes – and it is possible for this to happen even without human intervention.
Sophistication
 Anything that is complex is difficult to understand. Complexity, with regards to computer attacks, makes it difficult to detect and defend against these attacks. Many modern attacks are made to look legitimate, in other words trusted by your computer. Sometimes attacks enter a computer hidden inside a legitimate transaction, for example. In some cases computer attacks morph themselves so that computer anti-viruses will not recognize their "signature".
Anything that is complex is difficult to understand. Complexity, with regards to computer attacks, makes it difficult to detect and defend against these attacks. Many modern attacks are made to look legitimate, in other words trusted by your computer. Sometimes attacks enter a computer hidden inside a legitimate transaction, for example. In some cases computer attacks morph themselves so that computer anti-viruses will not recognize their "signature".
Simplicity of Attacks
Even you can be an attacker. Is it an instinct? Not really, you still have to learn the technique. In fact, if you know how to hack computers ethically, you will likely be able to prevent attacks on computer systems and networks. There are a few well known resources that will help you become an ethical hacker.
Click on the images/links below to check out these resources.

http://www.backtrack-linux.org/

http://www.metasploit.com/home/
Quick Detection of Vulnerablities
This means more "Active Attacking" vs. passive attacking. Active attacks are attacks on systems that have a known vulnerability, which may not have a fix until the computer gets "updated". 
Then, there are zero-day attacks. This is when a vulnerability of a system is discovered by thebad guys before the security community (the good guys) can fix it.
Click on the image or link below to read an article relating to a “critical” patch released by Microsoft that directly relates to this issue.
http://blogs.zdnet.com/security/?p=2853
Delays in Patching Products
Writing product updates immediately for every single malicious attack possibility is impossible.
Consequently, updating or patching a product has delays, thus allowing attacks to penetrate systems.
Distributed Attacks
When attacks come from another computer, the attacking computer may have other computers working with it. When this happens, it is diffcult to block the attack by blocking the source.
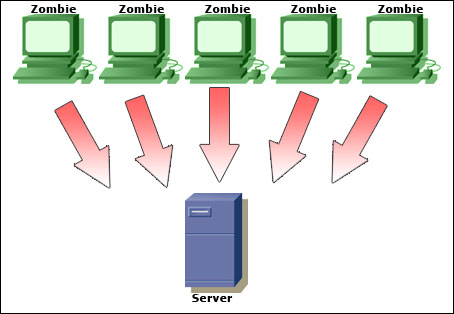
User Confusion
An uneducated guess can lead you to make the wrong decision regarding security.
 Assess the meaning and relevancy of security
Assess the meaning and relevancy of security