Attacks
Software makes your computer useful, right?
What if that software is Malware?
Malware is malicious code planted on your computer that gives your computer usefulness, but only to an attacker. It can give the attacker an alarming degree of control over your system, network, and data - without your knowledge.
Malware Viruses
 Topic 3-1: Discuss how viruses spread - student led discussion. Click on the FORUM image on the left to get more information on this discussion.
Topic 3-1: Discuss how viruses spread - student led discussion. Click on the FORUM image on the left to get more information on this discussion.
Malware Worms
A worm is like a virus, but does not need to have a carrier like a virus does. Worms take advantage of vulnerabilities in network applications and services and can spread through the Internet and Intranets (locally connected computers). Like viruses, it too will search for other systems with similar vulnerabilities.
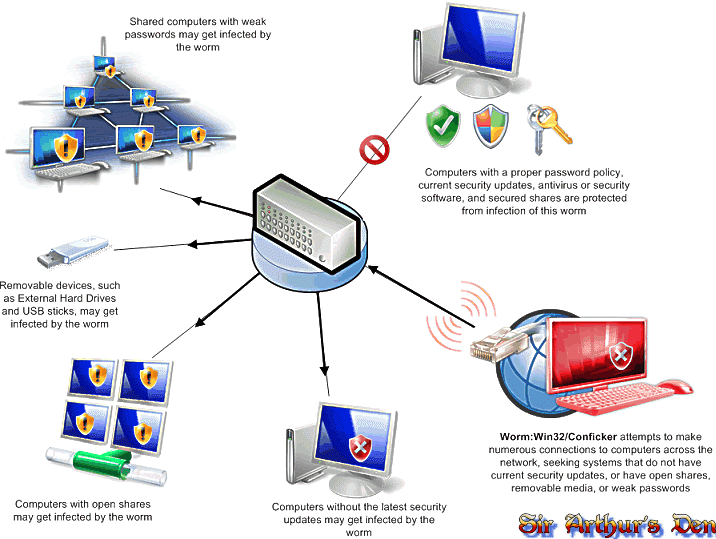
Malware Concealment
 Topic 3-2: Discuss various forms of viruses that "sneak" into your computer - student led discussion
Topic 3-2: Discuss various forms of viruses that "sneak" into your computer - student led discussion
Malware for Profits
 Topic 3-3: Discuss how malicious software (Malware) is used to make the attacker some money - student led discussion. Click on the FORUM image on the left to get more information on this discussion.
Topic 3-3: Discuss how malicious software (Malware) is used to make the attacker some money - student led discussion. Click on the FORUM image on the left to get more information on this discussion.
Other Desktop Security Attacks
Cell Phones
Cell phones work at a given frequency that is confined to a cell (shaped like a hexagon) that is about 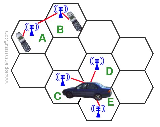 10 sq. miles. Each cell has a transmitter that communicates with a base station. Each base station communicates with a mobile telecommunications switching office (MTSO) which is the link between the cellar world and the wired world.
10 sq. miles. Each cell has a transmitter that communicates with a base station. Each base station communicates with a mobile telecommunications switching office (MTSO) which is the link between the cellar world and the wired world.
Many cell phones can send and receive messages and connect to the Internet. They can also store information, both financial and personal. Basically, function much like a desktop computer.
The additional threats for cellular handheld devices stem mainly from two sources:
1. Their size and portability
2. Their available wireless interfaces and
associated services.
Click on the image or link below to get more information.
http://coursecontent.ntc.edu/CIT/husband/pois/lp2/m12-cellphonethreats.html
Physical Theft
Small, portable devices such as laptops and cell phones are easy targets for theft. Sometimes these devices have valuable information on them that can damage personal identities or release corporate financial information and/or secrets.
Sometimes these devices have valuable information on them that can damage personal identities or release corporate financial information and/or secrets.
Theft of information can also come from computers sold or given away in legitimate transactions - such as rummage sales, charities, schools, selling online, or computer recycling centers.
Even though data may have been deleted, if the space where the data resided had not been wiped clean, the data can still be obtained.
 Investigate desktop computer system security and access controls
Investigate desktop computer system security and access controls