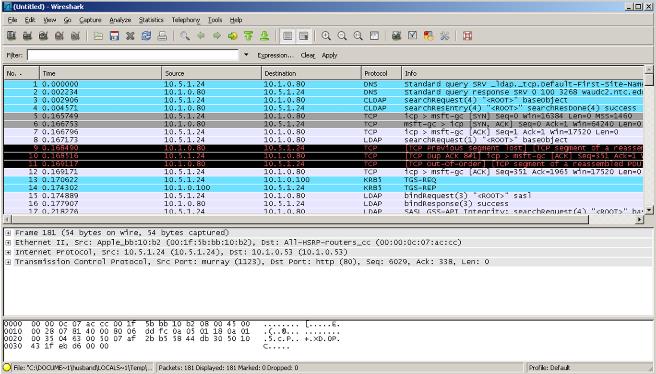
Eavesdropping
Transmissions can be captured using a
protocol analyzer/sniffer like Wireshark.
If the captured transmissions (packets) are not
securely encrypted with the latest encryption algorithm such
as WPA2, personal information can be obtained relatively
easy.
See image below.
Stealing Data
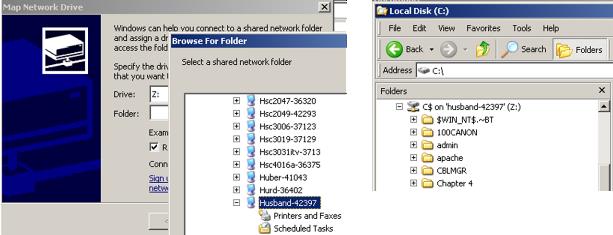
Once you successfully connect to a
wireless network you are essentially on that network.
If the network is not secured with pre-established
trust relationships, network sharing can become available to
you, thus enabling you to access network resources such as
shared folders.
Even the C: drive is shared by default.
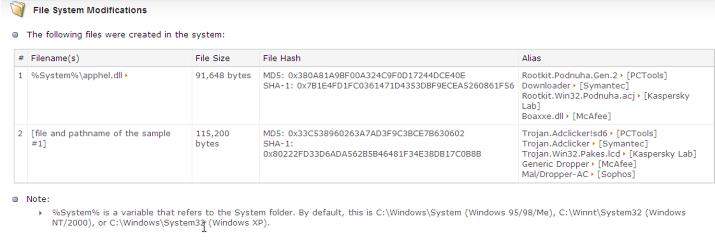
Injecting Malware
Once you are on a wireless network you are behind enemy lines (the firewall). This allows you to inject malware such as worms onto other network devices such as servers or workstations. From there, the worms can crawl to other devices in the network.
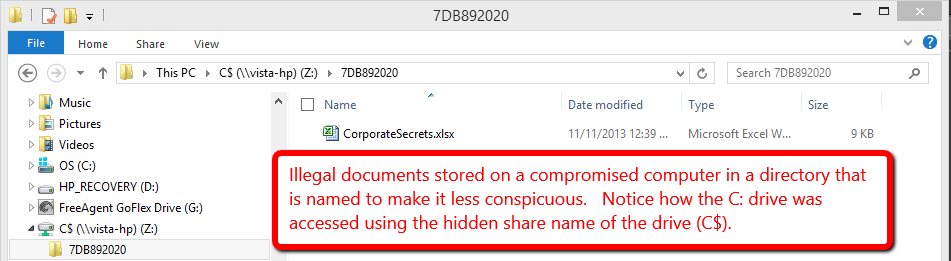
Storing Illegal Content
Criminals use the Internet and their
computer for illegal purposes.
The smart ones know that if illegal content is stored
on their own personal computer, it can be used as evidence
against them if a forensic investigation is ever made
against them.
To avoid being caught, criminals will store illegal
content on someone else’s computer without the owner of that
computer knowing it.
Once a criminal can access a wireless network and be
able to access a network share (with “write” access), this
process is relatively easy.
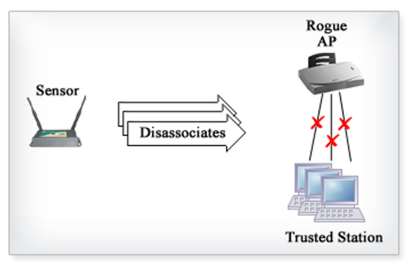
Launching Denial of Service
(DoS) Attacks
The intention of a DoS attack is to
saturate a network (either wired or wireless) or a device
(such as a web server) with traffic (network packets) to the
point that the network or device becomes useless to anyone
trying to access it.
If a criminal is connected to a wireless network,
they can flood the wireless network with traffic that will
bring the wireless access points to a crawl; DoS attacks may
also be targeted to other devices known on the wireless
network, such as servers.
An even more effective means of
disabling a wireless network is by establishing a
disassociation network frame
(packet) to disconnect legitimate wireless devices
from the network.
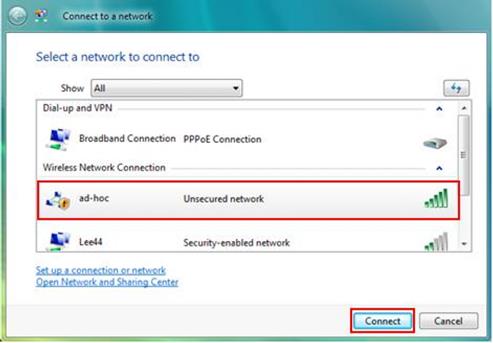
Impersonating a Legitimate
Network
If you were an attacker, wouldn’t it be
nice if you could get people to connect to you instead of
you connecting to them? This can actually be done from a
wireless PC that is configured to be an ad hoc wireless
network that allows other PCs to connect to it as if it were
a real network.
Once the connection is made, the attacker might be able to
inject malware or steal data.
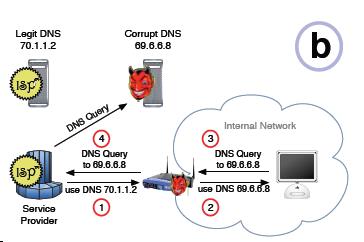
Steal Domain Name Service
(DNS) Traffic
Through a relatively simple Java script
that you unknowingly download from a compromised web server
somewhere on the Internet, your wireless access point, if
left at the default settings, can have its' internal
settings changed to reroute your name resolution requests to
a corrupt DNS server.
The way this works is simple.
Once you get compromised, the addresses (URLs) that
you type in your browser such as
www.paypal.com, will likely route you to an attacker's computer.
When this happens, the attacker's computer will
quickly Phish for personal information.
 MP5: Mobile Security
(Discussions - Specific Attacks)
MP5: Mobile Security
(Discussions - Specific Attacks)