Attacks
Passwords
There are three means by which you can prove to a computer that you are who you say you are.
- What you know.
- What you have.
- What you are.
What you know
For example, what you know could be your username and password; for the majority of people using a computer, this is all that is required. Requiring a password to login to many different computers often leads to password compromises because users make their passwords weak to aid in remembering them.
Access the links below to check the strength of your NTC password and to generate a strong password.
There are numerous reasons why people don’t use strong passwords and because of this, passwords are a frequent focus of attacks.
Password attacks include three common procedures:
- Brute force attack
- Dictionary attack
- Attacks using rainbow tables
Brute Force Attack
Generally, it would take a person too long to break a password by attempting to login multiple times with different passwords. Most times the computer would lock you out after a set number of times.
The trick: obtain the hashed (encrypted) password file from the computer you are trying to break into and use a specially designed program designed to formulate passwords, hash them, and then compare the manufactured hashed password with the hashes in the stolen password file. When a match is found, an attacker can then log into the account associated with the matched password - providing the user did not change their password since the file was stolen (and is the reason passwords should be changed often).
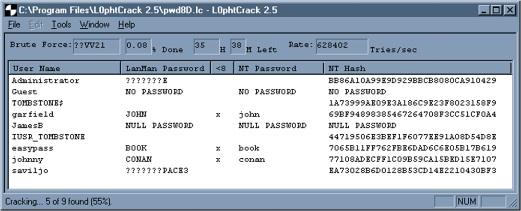
Dictionary Attack
This is another type of brute force attack that uses prebuilt dictionaries consisting of hashed values of common words. This database is compared against a stolen database of hashed passwords. If there are any weak passwords, these will be cracked within seconds.
A dictionary file can be tuned and compiled to cover words probably used by the owner of the account that a malicious user is going to attack. The attacker can gather information (via dumpster diving, social engineering, Internet research) to understand the user and then build a list of all unique words relating to the user.
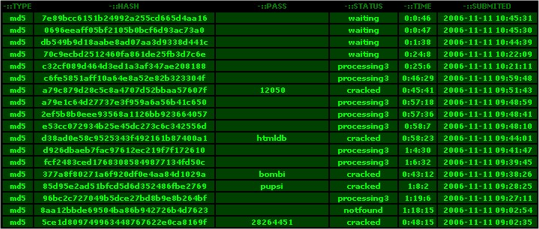
Rainbow Tables
With computer processors being really fast these days, the more common and preferred approach to password attacking is by using rainbow tables. These tables are prebuilt (and freely available on the Internet) databases of hashed values of every possible combination of passwords. This database is then compared against a stolen copy of a system’s hashed password database as would be done with a dictionary attack.
What you have
What you may have are tokens that you insert into the computer or wave in front of a scanner.

Who you are
Only you can provide your own finger print scan, retinal scan or palm scan.

Social Engineering Attacks
 Discuss social engineering attacks - student led discussion. Click on the image to the left to view the instructions.
Discuss social engineering attacks - student led discussion. Click on the image to the left to view the instructions.
 Explore common attacks directed at users and their personal security
Explore common attacks directed at users and their personal security